Not Shipped / Exploratory
Designing a compliance-aware digital gifting system
Exploratory systems design for enabling social value transfer in a regulated fintech environment.
Impact
Gifting could only exist if trust, growth, and compliance were designed together.
I designed a rule-based digital gifting system that balanced growth, trust, and regulatory constraints in a high-risk financial environment.
Rather than focusing on screens, the work defined system logic that made gifting expressive while remaining safe, auditable, and abuse-resistant.
Context and stakes
Gifting reframed routine value transfer into a social, high-risk interaction.
This work took place during early-stage exploration of a digital gifting feature within a regulated fintech platform. The concept reframed internal value transfers as intentional, social gifts rather than routine transactions.
The opportunity extended beyond peer-to-peer transfers. Gifting could support organic growth, referrals, and emotional engagement, but even small interaction decisions carried downstream compliance and trust implications.
The stakes were not whether gifting could feel delightful, but whether it could exist at all without introducing systemic risk.
Problem Framing
Gifting exposed system risks that standard transfer flows were never designed to handle.
At a surface level, the request was simple: let users send value to other people.
In practice, this raised a set of interconnected challenges:
- Transfers were limited to assets owned by the sender
- Referral incentives created strong motivation for abuse
- Email-based delivery introduced phishing and misdelivery risks
- Social identifiers raised privacy and discoverability concerns
- Identity verification introduced friction at the moment of delight
The core challenge was not designing a flow. It was designing a system of rules that balanced growth, trust, and compliance.
Constraints and Non-Negotiables
Friction could not be removed, but needed to be applied deliberately and transparently.
This exploration was shaped by several fixed constraints:
- Regulatory requirements around identity verification, custody, and transfers
- Anti-abuse safeguards for spam, referral gaming, and fake accounts
- Email as the primary off-platform delivery mechanism
- No automatic deposits for unverified users
- Existing referral logic already in production
The goal was not to eliminate friction entirely, but to apply it intentionally, in ways users could understand and trust.
Design Approach
Systems had to be designed before screens.
Rather than starting with UI, I approached the problem as a systems design exercise.
The focus was on defining:
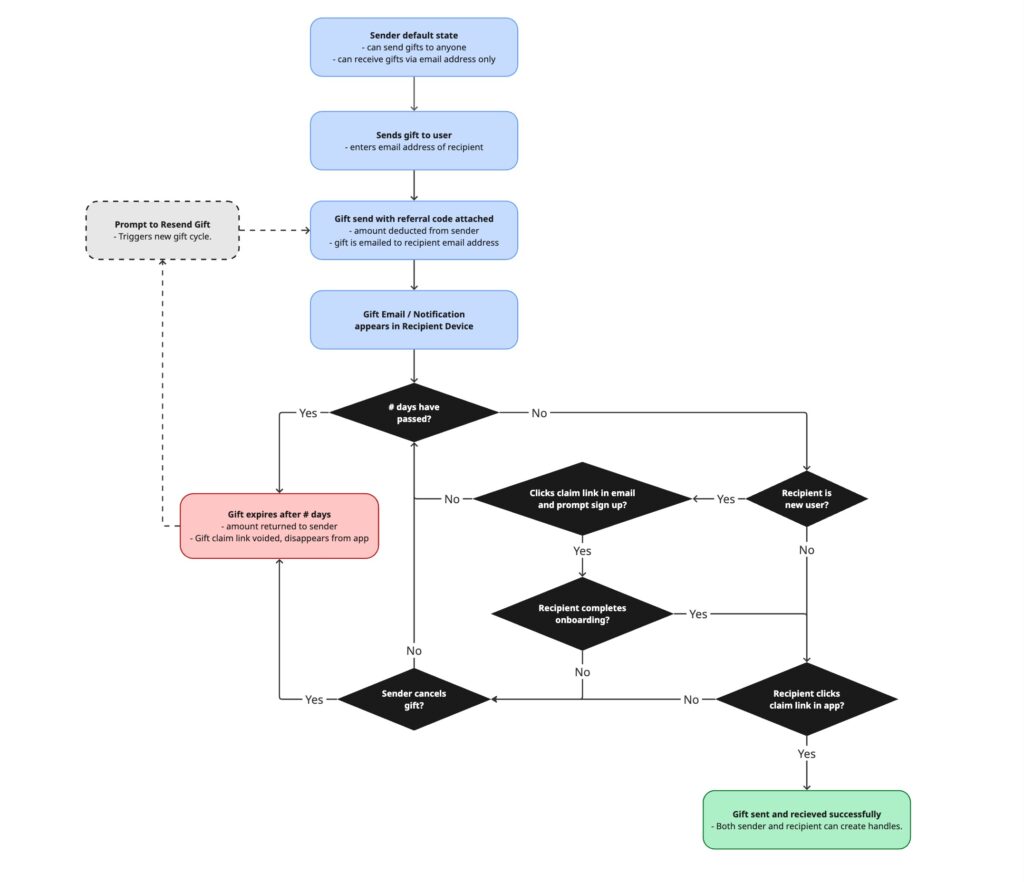
- Clear system states (funded, claimed, expired, cancelled)
- Explicit triggers that unlocked gifting power, referrals, or identity features
- Predictable behaviour for edge cases
- Guardrails that prevented abuse without punishing legitimate use
Key Systems Decisions
Each decision balanced user intent, regulatory constraints, and long-term system integrity.
#1 Gifting as a distinct, intentional action
Gifting was defined as separate from routine internal transfers, positioned as emotional and occasional, not transactional or habitual.
This reduced perceived frequency and risk while preserving intent.
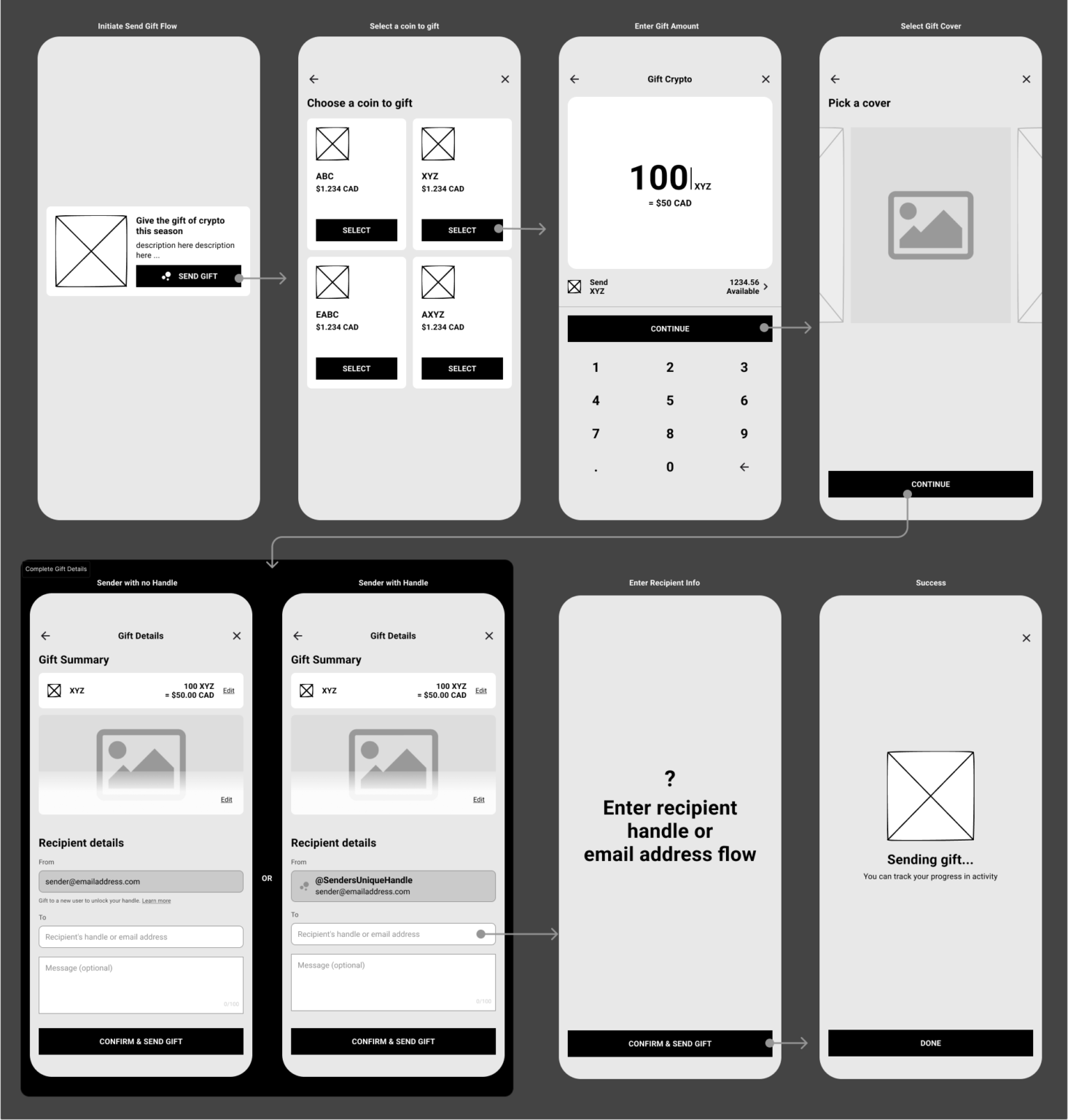
#2 Vaulted gifts with claim-based onboarding
Gifts were held in a vaulted state until recipients completed onboarding and identity verification.
Gifts were held in a vaulted state until recipients completed onboarding and identity verification.
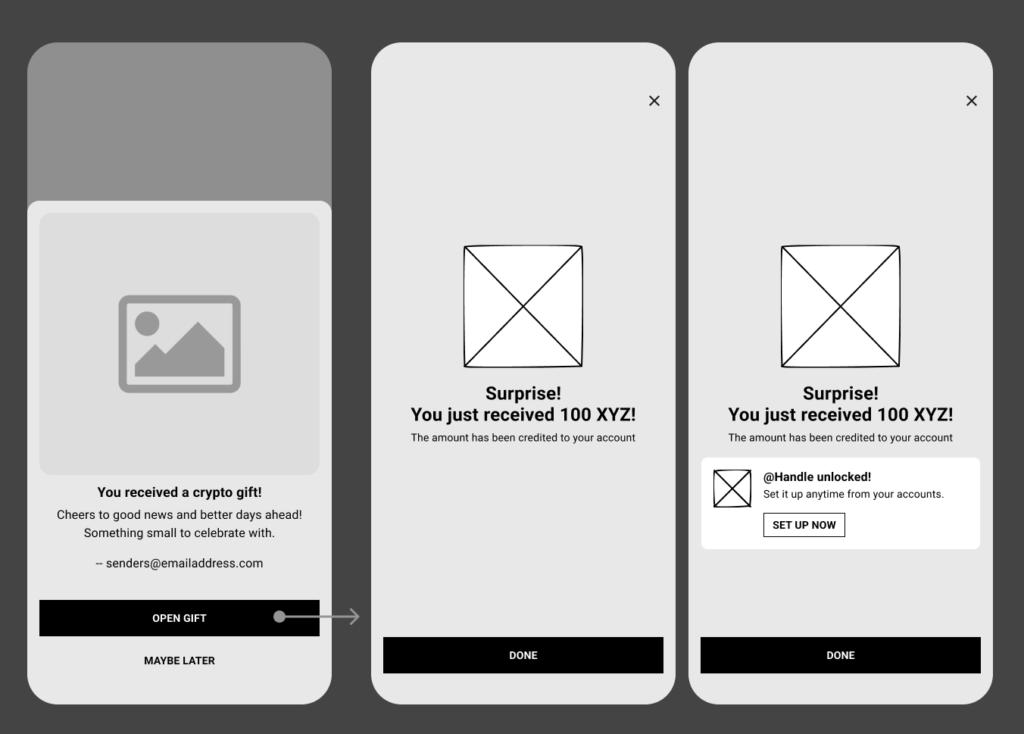
#3 Handles as a rewarded identity layer
Handles were earned, not cosmetic and were unlocked only after successful onboarding and locked once set.
This framed identity as a trust milestone, not a default.
#4 One-time unlocks to prevent gaming
Incentives were deliberately limited to first-time gift-driven onboarding.
Subsequent gifts behaved like standard transfers, removing spam incentives while preserving legitimate use.
#5 Controlled exposure at launch
Volume limits, frequency caps, and in-app gating allowed real behaviour to be observed before scaling, reducing risk while preserving intent.
Edge Cases as First-Class Inputs
Edge cases were designed explicitly, not treated as exceptions.
Rather than treating these as exceptions, each scenario had a defined outcome, reducing ambiguity for engineering and support.
The system explicitly accounted for scenarios such as:
- Multiple gifters targeting the same new user
- Gift links forwarded to unintended recipients
- Recipients onboarding outside the gift flow
- Expired or resent gifts
- Simultaneous gift attempts
- Abuse via fake or disposable email addresses
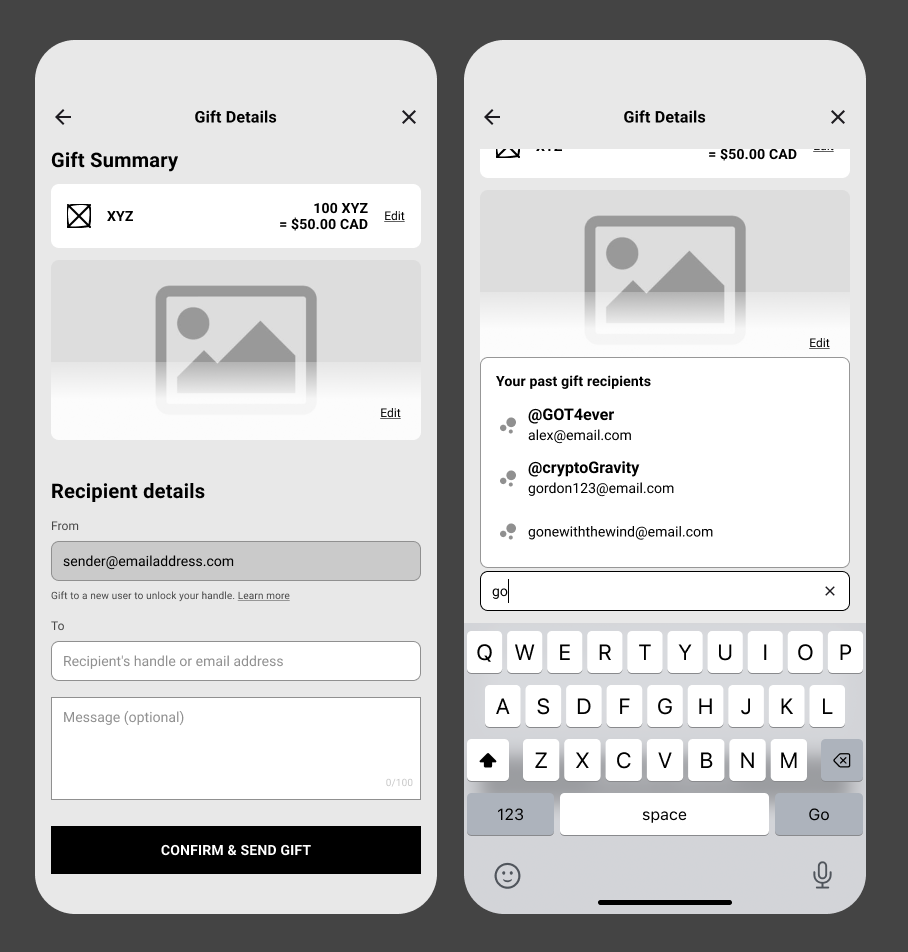
Recipient entry intentionally constrained discoverability: senders could only select known identifiers or manually enter new recipients, regardless of claim outcome.
My Role
I led product design and systems definition at the intersection of UX, strategy, and compliance.
My responsibilities included:
- Framing the problem under regulatory constraints
- Defining gifting rules, states, and transitions
- Mapping abuse scenarios and edge cases
- Designing unlock triggers and guardrails
- Translating abstract policy into actionable product logic
Outcome
The work created clarity—even without shipping.
Although the initiative was ultimately deprioritized, it delivered meaningful value:
- A shared mental model for how gifting could work safely
- Early visibility into compliance and abuse risks
- A reusable framework for future social or referral features
- Faster decision-making by making tradeoffs explicit
Reflection
Not all high-impact design work ships. Some of the most valuable work shapes how teams think, decide, and build.
This case reflects my strength in systems thinking, risk-aware design, and product judgment, particularly in constrained and regulated environments.